Introduction
AI is changing the threats while simultaneously empowering organisations due to its rapid evolution. AI is now being used by cybercriminals to automate attacks, produce extremely convincing phishing content, avoid detection systems, and take advantage of vulnerabilities at a rate never seen before.
As a result, organisations across sectors face a new class of risks that can disrupt operations, compromise sensitive data, and erode customer trust. Preparing for this next wave of threats requires more than standard cybersecurity practices.
Companies must strengthen their defence posture with AI powered security tools, continuous monitoring, employee awareness, and proactive threat hunting strategies.
By understanding how AI enabled attacks work and implementing resilient security frameworks, organisations can safeguard themselves against the growing sophistication of modern cyber adversaries.
How Rapidly AI Driven Cyber Crimes Are Emerging?
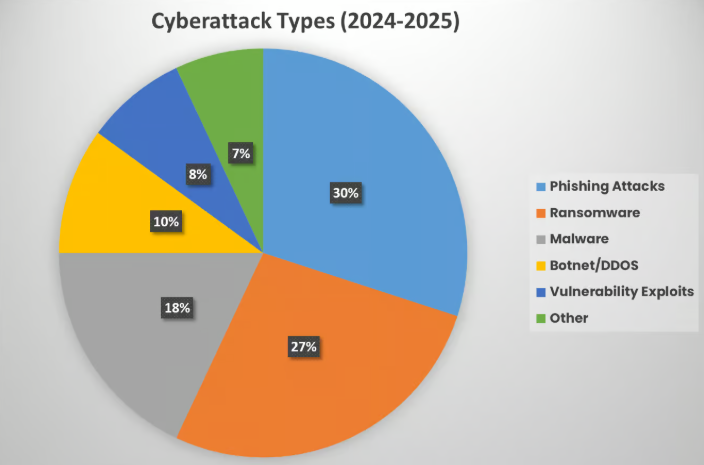
Image source : Market.us
In above image, it can be clearly seen the most prevalent type of cyber attacks, attackers are weaponizing both of the latest technologies that is automated intelligence and artificial Intelligence to enter the systems and alter data, disrupt critical infrastructure, or cause some level of automated ‘machine chaos’ intentionally, this just scratches the surface in terms of threats that can be facilitated by AI.
1. Rise of AI driven Attack Techniques
- Automated vulnerability detection
- Smarter malware and ransomware
2. Advanced Social Engineering Attacks
- AI generated phishing campaigns
- Voice & video deepfakes
3. Attack Automation and Scalability
- Fast execution of large scale attacks
- Low skill attackers gaining high skill capabilities
4. Exploiting AI Systems Themselves
- Data poisoning
- Model manipulation and extraction
How are These Threats More Dangerous?

1. AI attacks occur at unpredictable speed and scale, enabling hackers to fetch millions of user data in real time. Traditional protections cannot handle this and response time.
2. They launch very precise and individualized attacks, employing data patterns to hit with accuracy victims. This makes phishing and fraud, as well as impersonation, much more authentic and effective.
3. AI based threats are self evolving, learning from defenses and adapting in real time. Self upgrading malware is hard to identify and even more tougher to contain.
4. These threats really lower the barrier for cybercrime as AI gives opportunity to less skilled attackers who now have access to very advanced hacking tools. And that greatly increases the threats to all the organizations around the world.
5. Cybercrime in today’s time is more accessible than ever before, with AI tools able to automate many of the more complicated steps needed for hacking. This paves the way for attackers who have very less knowledge of hacking.
Most Common Type Of Cyber Security Attacks On The Organization
1. Malware
Cyberattackers use various types of malwares like spyware, virus to access the sensitive data of your company. They often send you a link or an anonymous attachment or sometimes through a fake id of your teammate. Once you click on the link, the malware will install itself without even your notice and steal your data without your notice.
2. Phishing
It’s a type of social engineering attack where attackers send fraudulent messages, often emails, that sounds like it is from a valid source. Its main purpose is to trick individuals into revealing sensitive information which could lead to attackers benefits like financial details and passwords and other users’ data.
3. Spoofing
Attackers also sometimes imitate people you know or companies to trick you into ultimately scamming you into sharing your personal information with them. There are many common techniques they use to operate this, like using software to call so that the receiver doesn’t see the number, creating fake sites, fake facial recognition and much more. With the help of AI they are getting smarter day by day.
4. Backdoor Trojan
There is always some kind of vulnerability in the software, hardware or networks, backdoor trojans use these weak points to give access to the AI cyber attackers and break into the system and install its malware very deep to steal the data even without awareness of the system.
5. Password Attack
This can be one of the easiest and simplest ways like guessing your password correctly or other techniques like keylogging where they keep an eye on you when you are typing your password and then identify it.
6. Internet Of Things Attack
It becomes very easy for cyber attackers to gain access to the data through inter communication between internet of things devices. This is due to the fact that all the IoT devices are connected to the internet and have limited security access.
7. Cryptojacking
Mining crypto currencies can cause significant operational cost, so cryptojacking helps the cyber attackers to avoid this expense. In this scam, they use the victim’s system or software to mine the cryptocurrency, stealing processing power without consent.
8. Drive By Download
This means that you think you have done nothing wrong and you will still be a victim of the cyber attack. This cyber attack happens when you download something from unknown sources or something which contains a virus or some other kind of malware.
How To Protect Your Organization
Implement AI native security solution
Use AI powered tools for the tasks like anomaly detection, threat hunting, and faster incident response, which can help keep pace with AI driven attacks. This involves using Agentic AI to proactively detect, analyze and respond to threats, including AI driven cyber attacks.
Leverage behaviour analytics
Deploy user and entity behaviour analysis(UEBA) to establish baselines for system and user activity, making it easier to detect deviations that could signal a threat. It uses AI algorithms to analyze data in real time, offering an additional layer of protection beyond the traditional rule based system.
Back Up Your Data
Backing up your data is crucial as you move it to a different and secure location like cloud or hard drive for storing it. This assists in ensuring that the data is safe and you can restore your data if it’s lost, any system failure or something else.
Update Your Software
The outdated systems are most prone to cyber attacks as they lack the latest robust security checks that can protect them against AI security threats. Whereas, updated systems are regularly updated and have capabilities that can protect your data from any kind of unknown threats.
Install A Firewall
Various anonymous attacks like, backdoor and denial of services can be prevented by installing a firewall. They operate by managing the website traffic through your system. Firewall will immediately stop any type of activity that it detects as suspicious.
Data Encryption
Data encryption is one of the popular ways to protect data. It is also vital for safeguarding your virtual data from any kind of unauthorised access and maintaining confidentiality. It is also important for compliance regulations, protecting data in transit and at rest.
Concluding Words
AI is now being used by cybercriminals to automate attacks, avoid detection systems, and take advantage of vulnerabilities at a rate never seen before. As a result, organisations across sectors face a new class of risks that can disrupt operations, compromise sensitive data, and erode customer trust.
A strong cybersecurity posture is essential to detect and prevent such threats and with the help of latest technologies, organizations can effectively secure their expanding attacks and strengthen their defence against data breaches.
FAQs
The most commonly targeted industries by AI cyber attacks are healthcare, manufacturing, and financial services. The reason these sectors are largely targeted is because they hold valuable data and there are high chances that these industries will pay any amount of data to protect their sensitive information.
With the help of continuous monitoring of network trafficking and system logs and using various tools and employee training, enterprises can detect cyber attacks before they cause damage.
The cyber insurance helps the firm in covering the losses related to incident response, data restoration, business interruption, and legal abilities. It also pays for data recovery and system repairs, enabling a faster and less disruptive return to normal operations.
It very effectively enhances threat detection and responses by speeding the process of analysis, identification of threats and also recognising the false positives and automating the responses.





